近日, Apache Log4j 的远程代码执行最新漏洞细节被公开,攻击者可通过构造恶意请求利用该漏洞实现在目标服务器上执行任意代码。可导致服务器被黑客控制,从而进行页面篡改、数据窃取、挖矿、勒索等行为。

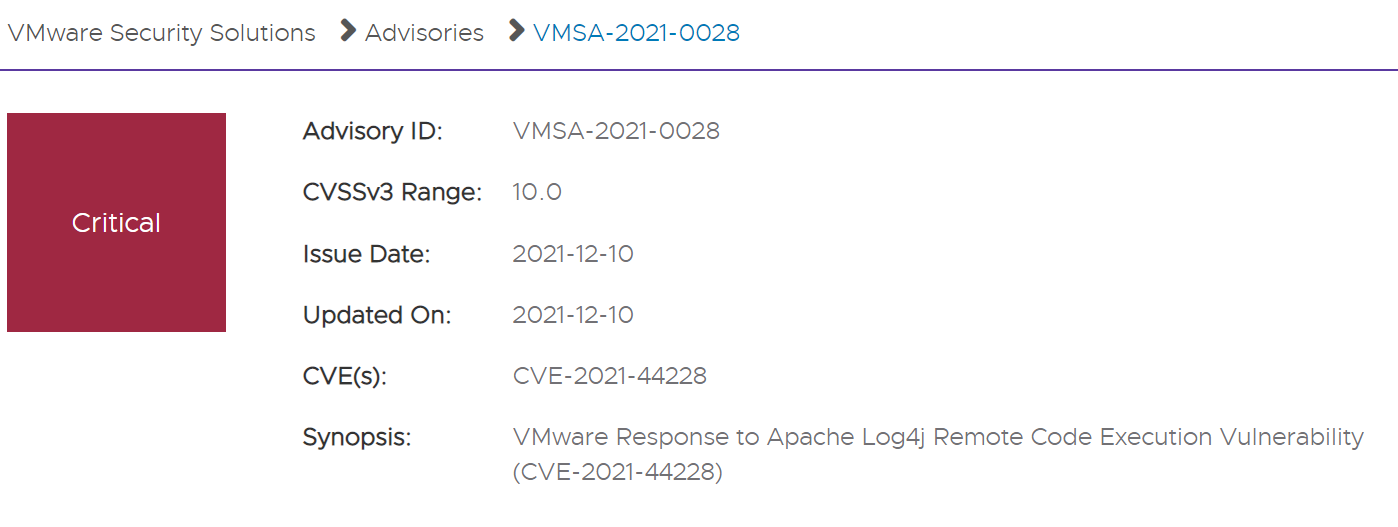
12月10日,VMware官方发布安全通告,通告了受影响的VMware产品。
一、受影响的产品:
VMware Horizon
VMware vCenter Server
VMware HCX
VMware NSX-T Data Center
VMware Unified Access Gateway
VMware WorkspaceOne Access
VMware Identity Manager
VMware vRealize Operations
VMware vRealize Operations Cloud Proxy
VMware vRealize Log Insight
VMware vRealize Automation
VMware vRealize Lifecycle Manager
VMware Telco Cloud Automation
VMware Site Recovery Manager
VMware Carbon Black Cloud Workload Appliance
VMware Carbon Black EDR Server
VMware Tanzu GemFire
VMware Tanzu Greenplum
VMware Tanzu Operations Manager
VMware Tanzu Application Service for VMs
VMware Tanzu Kubernetes Grid Integrated Edition
VMware Tanzu Observability by Wavefront Nozzle
Healthwatch for Tanzu Application Service
Spring Cloud Services for VMware Tanzu
Spring Cloud Gateway for VMware Tanzu
Spring Cloud Gateway for Kubernetes
API Portal for VMware Tanzu
Single Sign-On for VMware Tanzu Application Service
App Metrics
VMware vCenter Cloud Gateway
VMware Tanzu SQL with MySQL for VMs
vRealize Orchestrator
VMware Cloud Foundation
(Additional products will be added)
二、解决方案
官方正在陆续修复,部分产品已经公布临时解决方案。
| 产品 | 版本 | CVE编号 | 已修复版本 | 临时缓解措施 |
| VMware Horizon | 8.x, 7.x | CVE-2021-44228, CVE-2021-45046 | 8.4.0,7.13.1,7.10.3 | KB87073 |
| VMware vCenter Server | 7.x, 6.x | CVE-2021-44228, CVE-2021-45046 | 7.0.3,6.7U3q,6.5U3s | KB87081 |
| VMware Unified Access Gateway | 21.x, 20.x, 3.x | CVE-2021-44228, CVE-2021-45046 | 2111.1 | KB87092 |
| VMware vRealize Operations | 8.x | CVE-2021-44228, CVE-2021-45046 | 8.6.2 | KB87076 |
| VMware vRealize Log Insight | 8.x | CVE-2021-44228, CVE-2021-45046 | 8.6.2 | KB87089 |
三、升级参考文档:
vCenter Server 升级方法:如何升级vCenter(VCSA)补丁?
vCenter 6.x 临时处理方法:vCenter Server 受Apache Log4j2漏洞影响临时解决方法
Horizon更新:VMware Horizon连接服务器升级步骤
vRealize Operations 更新:升级VMware vRealize Operations Manager补丁

发表评论